The other day I received a nervous call from one of my clients: “my email has been hacked“.
Apparently, someone had hacked into my client’s account and sent an email to the organization’s registrar requesting financial information. For context, my client is the president of the organization (keep reading to learn why this is important).
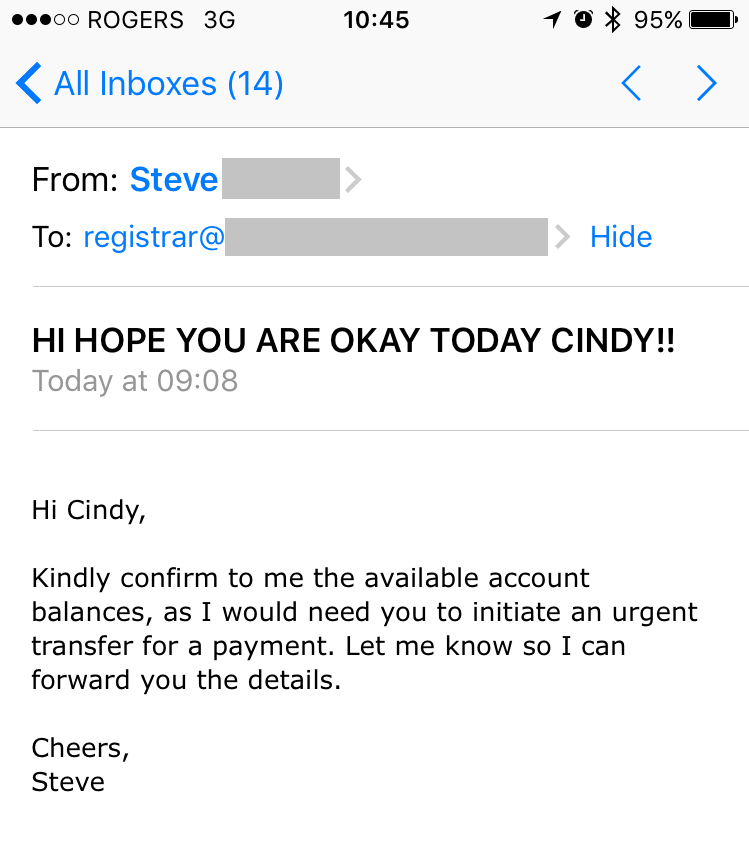
Apart from the ALL CAPS in the subject line, the email looks legit. It includes the real name of the recipient, Cindy, and is signed off by Steve.
You see, there is a new email scam going around in 2017 that poses a real danger to corporations and business like yours.
About the Scam
There is a spamming tactic that goes a little something like this: Someone high up in the company, like a CEO or president requests the issuance of a wire transfer from someone in the financial department of the company, someone with the authority to issue payments.
This was written about by Symantec on their blog. Read Scammers Pose as Company Execs in Wire Transfer Spam Campaign.
So, in fact, Steve’s email account was not hacked at all, but only gave the appearance that it was.
How We Spotted the Scam
What gave it away was the “Reply-to” address:
presidentt1@mail2president.com
For the record, this is not Steve’s company email.
Although, at first glance, Cindy would see that the email appears to come “From” Steve’s business email; part of the scam is to fake the appearance of this.
Depending on your email client (Outlook, Gmail, Hotmail), you can pretty easily see who the “Reply-to” recipient is. When in doubt – especially if you receive a similar email – do a little digging and try to locate this.
More often than not, once you hit “Reply” you can see more information about where the email came from and where it is going, including the “Reply-to” address.
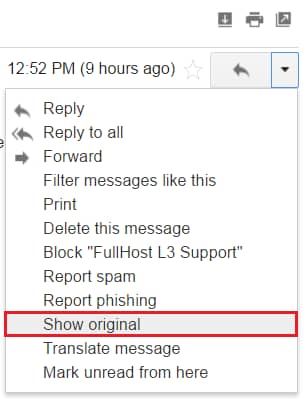
In most email clients, there is also an option for viewing the email header information. This information is a detailed summary of all the stops this email took during its trip to your inbox.
For example, in Gmail, you can click on the drop-down arrow beside the “Reply” arrow and select “Show Original”. This will display a detailed summary of the path this email took to land in your inbox as well as the Sender and Recipient information.
Further Sleuthing
But how did the Scammer know the “From” address, the name of the president and registrar?
It doesn’t take a genius to realize that any company with a website typically lists this information publicly, that is, the names of those in the organization, their roles, and contact emails.
All it takes is a little research work to piece together who’s who in the organization; this is exactly what these spammers do to mimic these company executives.
You’ve been warned!




